Each one of us is a system administrator: for at least your workstation (or notebook) you can decide when and how to administrate it. In the special case in which you are being elected to administer servers too, the matter becomes thorny: what is the workflow in terms of patching, time of reaction to security issues and, in general, when and how to install updates?
Some distributions offer the concept of automatic (or unattended) upgrades: install automatically a subset (or all) the available updates via the package manager. This particular subset can be specified by the system administrator, a notable example would be the subset of security updates.
The approach is, of course, debatable: should you use it for a critical server? What happens if the upgrade goes south? Would this approach scale?
The answer is, nevertheless, debatable: it depends. You are not required to use automatic updates, but installing security patches automatically might make sense in some non-mission-critical situations. You can read an opinionated list of reasons to use automatic updates, as well as an equally opinionated list of reasons NOT to use automatic updates.
In this post, I am going to present the three approaches for automatic updates offered in:
- openSUSE
- CentOS and Fedora
- Debian and Ubuntu
and how I setup them for my own “very special, do not try this at home” situation, which means that servers always install only security updates automatically.
openSUSE
openSUSE can schedule automatic updates via Automatic Online Update.
Take a look at the documentation: everything is already well documented, you just need to the package with:
# zypper install yast2-online-update-configurationand then, to configure it:
# yast2 online_update_configuration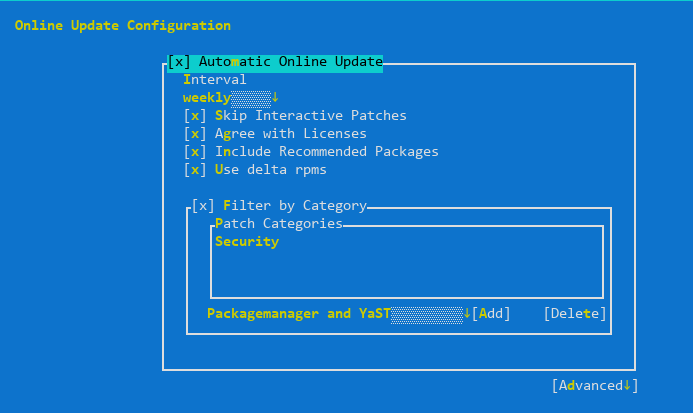
The servers must weekly check and install only security updates automatically (category “Security”), except the ones declared as “Interactive”. From the documentation:
Sometimes patches may require the attention of the administrator, for example when restarting critical services. For example, this might be an update for Docker Open Source Engine that requires all containers to be restarted. Before these patches are installed, the user is informed about the consequences and is asked to confirm the installation of the patch. Such patches are called “Interactive Patches”.
When installing patches automatically, it is assumed that you have accepted the installation of interactive patches. If you rather prefer to review these patches before they get installed, select Skip Interactive Patches. In this case, interactive patches will be skipped during automated patching. Make sure to periodically run a manual online update, to check whether interactive patches are waiting to be installed.
Skipping interactive patches absolutely makes sense to me, as well as using delta RPMs (to save bandwidth), auto-agreeing with licensing and including recommended packages.
Update: Richard reminded me that if you are running Leap or Tumbleweed with transactional updates, you can take advantage of automatic transactional updates; rebootmgr will take care of automatically reboot the machine in case any transactional updates were installed.
CentOS version <= 7
The package that enables automatic updates is called yum-cron. To install it:
# yum -y install yum-cronThe configuration file (/etc/yum/yum-cron.conf) is self-documenting: just open it in an editor and begin tweaking. In my case, to check and install only security updates I just changed the following two lines:
update_cmd = security
apply_updates = yesFinally, make sure that the corresponding service is enabled:
# systemctl start yum-cron.serviceFedora and CentOS version >= 8
Fedora automatic updates are enabled by installing the dnf-automatic package:
# dnf install -y dnf-automaticAs with CentOS, I just changed the configuration file (/etc/dnf/automatic.conf) to install security updates only:
upgrade_type = securityAfter the configuration, start the service:
# systemctl enable --now dnf-automatic.timerDebian and Ubuntu
Debian and Ubuntu make use of the unattended-upgrades package in order to enable automatic updates. Let’s begin with installing it:
# apt install unattended-upgradesIt is configuration time: make sure to enable the update of package lists and perform the upgrade in /etc/apt/apt.conf.d/20auto-upgrades:
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Unattended-Upgrade "1";Now enable the repository from which updates can be installed in /etc/apt/apt.conf.d/50unattended-upgrades; in our case, only the security repository:
Unattended-Upgrade::Origins-Pattern {
"origin=Debian,codename=${distro_codename},label=Debian-Security";
};Conclusions
Every distribution offers then its own tweaks (like email notifications when updates are ready and when are installed), package exclusions based on package names, install updates at shutdown time and whatnot: be sure to read the documentation! The examples are just a starting point.
Happy automatic patching!
Great! the latest version of CentOS uses dnf now, so that needs updating.
You are right: I updated the post to reflect the situation for CentOS version 7 and version 8 (same as Fedora with dnf-automatic). Thanks!